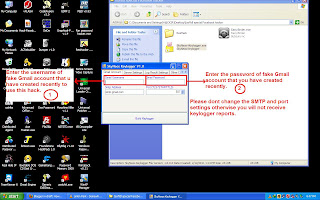
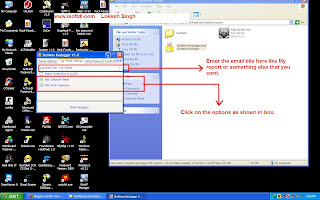
Tools Description of System Hacking - Keylogger
Actual Spy Keylogger
Actual Spy - is a keylogger which allows you to find out what other users do on your computer
in your absence. It is designed for the hidden computer monitoring and the monitoring of the
computer activity. Keylogger Actual Spy is capable of catching all keystrokes, capturing the
screen, logging the programs being run and closed, monitoring the clipboard contents.
Ardamax Keylogger
Ardamax Keylogger is a keystroke recorder that captures user's activity and saves it to an encrypted log
file. The log file can be viewed with the powerful Log Viewer. Use this tool to find out what is happening
on your computer while you are away, maintain a backup of your typed data automatically or use it to
monitor your kids. Also you can use it as a monitoring device for detecting unauthorised access. Logs can
be automatically sent to your e-mail address, access to the keylogger is password protected. Besides,
Ardamax Keylogger logs information about the Internet addresses the user has visited.
Ghost Keylogger
Ghost Keylogger invisibly captures all keystrokes to a logfile or optionally sends them to a predefined
email address
Golden Keylogger
If you have teenage son or daughter (some of us have both), then you know how crazy they are about
chatting and instant messaging. We know that it's not all that innocent. TV news are packed with stories
when strangers tried to take advantage of innocent children by using internet chats and IM (instant
messaging). The problem is so big that FBI has a task force that works 24 hours a day 365 days a year.
Another problem that recently got a lot of publicity is bullying and name-calling with instant messengers.
While your kids may not be honest with you about who they are chatting with and what they discuss, you
have the way to know exactly what's going on without invading your kids' privacy. How? Golden
Keylogger!
Home Keylogger
Home Keylogger is intended for interception and recording in a file of everything that is entered from the
keyboard. The program is able to work in the hidden mode and to emerge on pressing a combination of keys.
Home Keylogger is able to present the recorded data in a neat way that is easy to read but at the same time fixing
exactly every event that has been done. By constantly using this program you will save your time by preventing
accidental data damage and loss that is frequently caused by the use of Internet. You can immediately restore the
text which was typed yesterday, the day before yesterday, or one week ago. Home Keylogger will also help to
recollect passwords that you have forgotten or to recover lost e-mail.
Invisible Keylogger
Invisible is a full featured pc and Internet activity monitoring software that enables you to record
everything on your pc. This product is extremely stealth and packs a big punch.
KGB Keylogger
Imagine you are writing an e-mail message. Then you click a wrong button or your e-mail client hangs and
you have to write the same text from scratch. Sounds familiar? With KGB Free Keylogger, you will never
lose any of your text, whether it was typed in an e-mail client, a text editor, an on-line form or anywhere
else. This free program logs everything you type. Get your passwords, registration keys and other info
safely logged.
Invisible Keylogger
Software has enhanced feature to record keystroke activities in encrypted log file with option to
mail the log report at your specified email address. Helps to provide full control on your PC and
act as powerful surveillance utility for Home and Office usage.
Remote Keylogger
Powerful and easy to use Computer Keylogger is a Stealth Keylogger to monitor your PC being
hidden while maintaining absolute secrecy in your absence.
Soft Central Keylogger
SC-KeyLog PRO is a powerful digital surveillance monitor that logs computer activity for later review.
Our spy program allows you to secretly record computer user activities such as e-mails, chat
conversations, visited web sites, clipboard usage and more in a protected logfile. SC-KeyLog PRO even
captures Windows user logon passwords!
Stealth Keylogger
Keylogger Software efficiently monitors the entire typed keystrokes activities of external user
performed on your PC or Laptops. Easy to use utility records each keyboard entries including
composed emails, chat records, typed web url’s, passwords, text etc.
Software has enhanced feature to record keystroke activities in encrypted log file with option to
mail the log report at your specified email address. Helps to provide full control on your PC and
act as powerful surveillance utility for Home and Office usage.
Winvestigator Keylogger
Winvestigator™ is a user monitoring program that starts on boot, and runs undetectable in Windows. It
even takes pictures so you can really see what is going on! Although powerful, this program was designed
to be easy to use. Offering a web page style interface and a thorough help resource.
Winvestigator can send the log over email so you can monitor a computer without having to physically
access it.
Download tool from below URL